Add auth to your app and get built-in cyber immunity
Everything you'd expect from modern IAM, but with security built into the fabric
Technology validated by universities & global experts









ADD
Insurance Protection
Interested in complementing cryptographic assurances with the gold standard in cyber-insurance?
Contact usAPPLY FOR
Alpha Program
Apply for access to our direct engagement program and have the Tide team assist with building your dream platform.
Read moreBuild fast. Sleep easy.
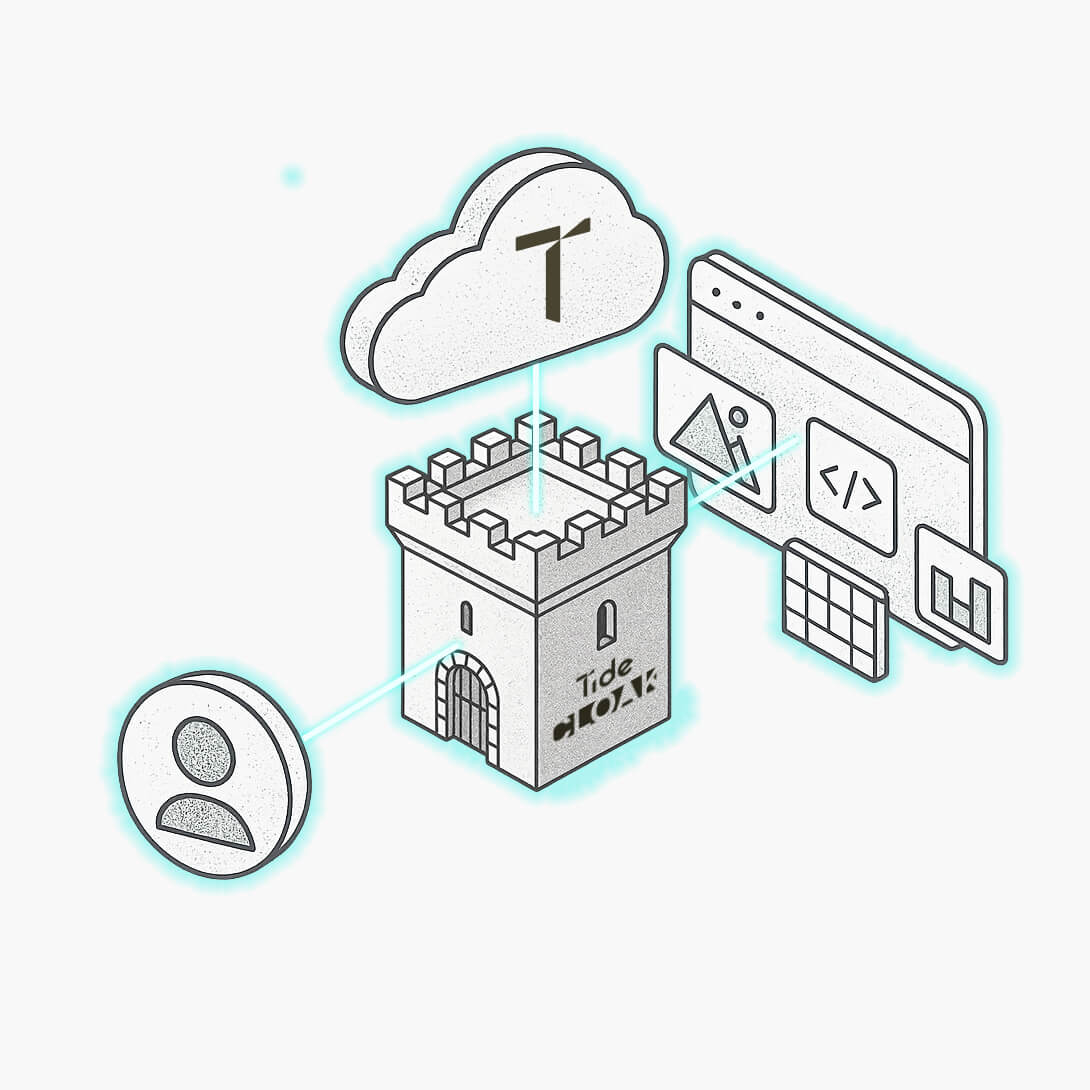
TideCloak is a drop-in Keycloak-compatible IAM immune by Tide's Cybersecurity Fabric. It locks identities, data and access rights with keys no one - not admins, your cloud, vendors (even us) - can ever hold, so your controls keep working even in worst-case breaches.
BYOiD
Empower users to "bring their own identity" only they control, and sign-in with absolutely no change to the user experience. All, with the robust security of a digital wallet. No one is holding a repository of passwords any longer. Users can never be impersonated. Compromised users pose no risk to others. Circumvention of the authentication process is no longer possible.
Tamper-proof Authorization
Flexible, policy-driven authorisation that's sealed by an authority key no one ever holds and no single entity can abuse. Every seal is a proof that validation was successfully completed in a incorruptible process.
Quorum Enforced Governance
No more "god-mode". A compromised administrator cannot abuse their privilege, workflow processes cannot be circumvented, and accountability is baked in.
Immunity-Sealed E2EE
End-to-End Encryption that binds each session to a one-time, device-specific key and uses it to create a verifiably secure tunnel to your service - ensuring only the legitimate client can access the data, and hermetically sealing the loop between authentication, authorization, authority, and secure service consumption.
Comprehensive IAM features
Add authentication, authorization and user data security for your applications with ease. Built on top of Keycloak, RedHat's enterprise-grade Identity and Access Management solution GitHub Stars33k, TideCloak adds a plug-and-play provable-immunity layer to the comprehensive feature set below.


BYOiD
Empower users to "bring their own identity" only they control, and sign-in with absolutely no change to the user experience. All, with the robust security of a digital wallet. No one is holding a repository of passwords any longer. Users can never be impersonated. Compromised users pose no risk to others. Circumvention of the authentication process is no longer possible.

Tamper-proof Authorization
Flexible, policy-driven authorisation that's sealed by an authority key no one ever holds and no single entity can abuse. Every seal is a proof that validation was successfully completed in a incorruptible process.

Quorum Enforced Governance
No more "god-mode". A compromised administrator cannot abuse their privilege, workflow processes cannot be circumvented, and accountability is baked in.

Immunity-Sealed E2EE
End-to-End Encryption that binds each session to a one-time, device-specific key and uses it to create a verifiably secure tunnel to your service - ensuring only the legitimate client can access the data, and hermetically sealing the loop between authentication, authorization, authority, and secure service consumption.

Comprehensive IAM features
Add authentication, authorization and user data security for your applications with ease. Built on top of Keycloak, RedHat's enterprise-grade Identity and Access Management solution GitHub Stars33k, TideCloak adds a plug-and-play provable-immunity layer to the comprehensive feature set below.

Comprehensive standard feature set
Single Sign-On (SSO)
One login across all your apps.
Open Standards
OIDC and OAuth 2.0 compatible. Future SAML support.
User Federation
Sync with LDAP/Active Directory.
Centralized User Mgmt
Users, groups, and role mapping in one place.
No Lock-In
Easy on and offboarding with no business continuity threat.
Varied Authorization Models
RBAC, ABAC, UBAC, CBAC.
Zero Knowledge Password auth
No artefact stored anywhere.
Passwordless
2nd factor with security keys and biometrics.
User Self-Service
Account console for profile, credentials, sessions, consents.
Admin Console & API
Full admin UI plus REST Admin API.
Session & Token Control
Rotation, revocation, token exchange, remember-me.
Theming & Branding
Customizable UI.
Adapters & Integrations
Client libraries for popular stacks.
Kubernetes-Ready
Container-friendly with HA clustering options.
Audit & Events
Admin/user event logs for compliance and troubleshooting.
Extensible by Design
SPI plugins for custom authenticators, mappers, providers.