Trust Your Key With a Trustless Bot
Blockchain is often touted as the most secure network ever created. It’s not unusual to hear people describe it as ‘Unhackable’, ‘Immutable’, ‘Tamper-proof’, ‘Trustless’. Whilst these are all powerful and aspirational qualities, anyone using any form of cryptocurrency today, knows that security is still an issue at the heart of the industry.
For something considered so secure, it seems quite contrary when confronted with reports such as, in 2018 $865 million was stolen from cryptocurrency exchanges.
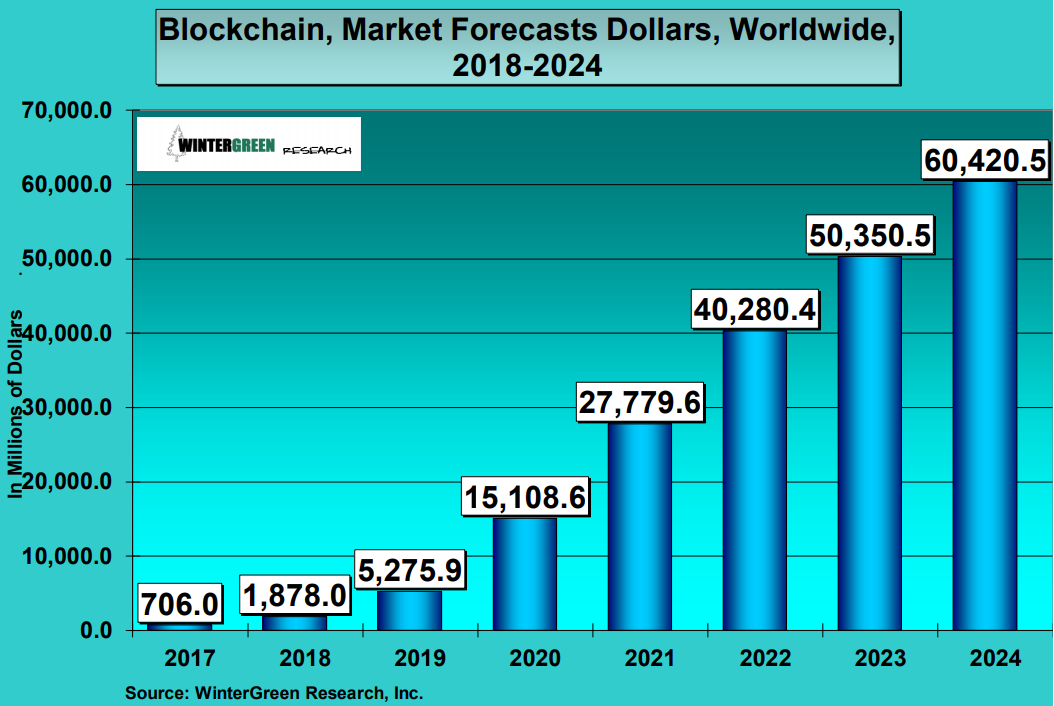
Source- https://www.ibm.com/downloads/cas/PPRR983X
There’s a saying in the crypto world: “not your keys, not your coins!” Meaning, the security of crypto is only maintained due to the strength of keys — hand those keys to anyone and you may well be handing them your crypto assets for good. While that places the burden of responsibility on you, it guarantees your crypto assets are safe.
Unfortunately, it also means that without your explicit involvement, or at the very least, your wallet being available online, you cannot interact with the blockchain. Which means your assets can’t be moved or traded. On the surface, it’s not that bad, except for when it becomes time-consuming, repetitive or time sensitive. Smart-contracts allow some automation but their limitations are significant, and so far don’t come close to replicating the functionality we’re accustomed to with centralized systems. The parameters of a smart contract must be predefined, which means an automated interaction can’t adapt to new circumstances. For example a specific fund amount must be locked into the contract for initiation. Perhaps more significant, is a smart contract’s inability to keep secrets or use a secret in an automated interaction. For example, a smart contract can’t hold a treasure map (or instructions) secret and revealed to only a particular party if they answered a riddle correctly. Neither the map nor the riddle answers can be stored in a smart-contract because of its inherent transparent, deterministic and immutable design.
Imagine if you could trust your wallet key to someone, with the assurance it’ll only be used per your explicit instructions? You could have your funds deployed when you’re not available. Trade variable amounts on different exchanges. Unlock a digitally-enabled door in your absence. Handle your estate if something happens to you. Allow for lawful backdoor access to your account if approved by an elected panel to enforce justice. That requires a lot of trust.

In fact, similar automation already exists in the form of trading bots. Trading bots automate cryptocurrency trades based on predefined parameters. They allow users to make trades 24 hours a day and stay tuned in to the market even while asleep. Which is important as unlike traditional stock markets, the crypto market never closes. With the correct criteria, bots enable traders to stay in the game at all times and even execute faster, more efficient and precise trades.
Unfortunately, these bots require access to your private key or its equivalent API key, presenting a trust issue and security vulnerability. But what if it didn’t?
What if a bot was was trustless?
Tide is using crypto-tokens and crypto-wallets to manage access permissions to your personal data. Individuals use their crypto-keys to provide explicit consent to organizations seeking access to their details. The operation of granting access manually becomes quite tedious if you’re being asked several times a day. If you’re being generously compensated for it, you wouldn’t necessarily want to categorically deny those requests either.
Not having the time to respond to each individual request is going to result in missed opportunities, loss of income or skipping an awesome deal. It’s like hand signing all your Christmas cards: fine to do once a year but every day becomes impractical. If you know what data you’re comfortable sharing with particular types of organizations, shouldn’t you be able to give your on-going automatic consent?
Tide developed a technology that enables just such automation over their fully decentralized crypto-key management platform. Effectively giving rise to a trustless bot, or in other words an individual’s Delegated Automated Trustee on the blockchain (a DAT). In the Tide ecosystem, this means an individual simply provides parameters to the DAT to trade permission to access their personal data automatically on his or her behalf, as long as their criteria are met.
The magic ingredient to this decentralized solution is its ability to be a custodian of a crypto-key. In principle, this is achieved by splitting pieces of a key among a group of nodes. No single node (or subgroup) have any access or knowledge of the whole key, or the authority to act on its own, rendering malicious access to your key virtually impossible. Using secure multi-party computation, these nodes can act in a swarm to perform functions with the authority of the key on the user’s behalf. The technology is detailed in section 3.3.3 of the Tide Technical whitepaper.
Outside of managing automated access to personal data, this technology opens up a world of trustless opportunities, including decentralized authentication and password or key recovery. It enables businesses processes requiring ongoing access to your crypto-assets (monetary or otherwise) to operate without delay as long as the access is within your defined parameters as a customer, patient, citizen or subscriber.
The DAT can be used for many other wallet automation functions that weren’t feasible before, such as enabling automated trading bots access to your funds without ever having access to your key. Automated trading on decentralized exchanges can be achieved with a new tier of security. Trustlessness as it was intended.
While centralized solutions to these challenges are common (and vulnerable), fully trustless alternatives have so far proven unwieldy, complex or have significant limitations. These flaws hinder mainstream audience adoption.
Whether in a personal data ecosystem, crypto trading realm or elsewhere, it will be interesting to see whether this novel approach to trustless key management is the missing key to decentralization becoming a practical alternative to centralized systems.