KeyleSSH: A PAM With No Single Point of Vulnerability
Built using Tide's Ineffable Cryptography, KeyleSSH eliminates the "keys to the kingdom" problem that plagues traditional PAM solutions.
Read more →

Add authentication with the authority layer
no one can compromise.
Trusted by Devs from






Secure apps and APIs with only few lines of code. Language agnostic. Open Code. Self sovereign management. Locally hosted. Instant protection. End-to-end verifiability.
Designed to withstand even a vendor breach.
sudo docker run \
--name mytidecloak \
-d \
-v .:/opt/keycloak/data/h2 \
-p 8080:8080 \
-e KC_BOOTSTRAP_ADMIN_USERNAME=admin \
-e KC_BOOTSTRAP_ADMIN_PASSWORD=password \
tideorg/tidecloak-dev:latestTIDECLOAK
TideCloak is an IAM server integrated with Tide ineffable authority technology to deliver provably-secure applications.
LEARN MORE ABOUT TIDECLOAK →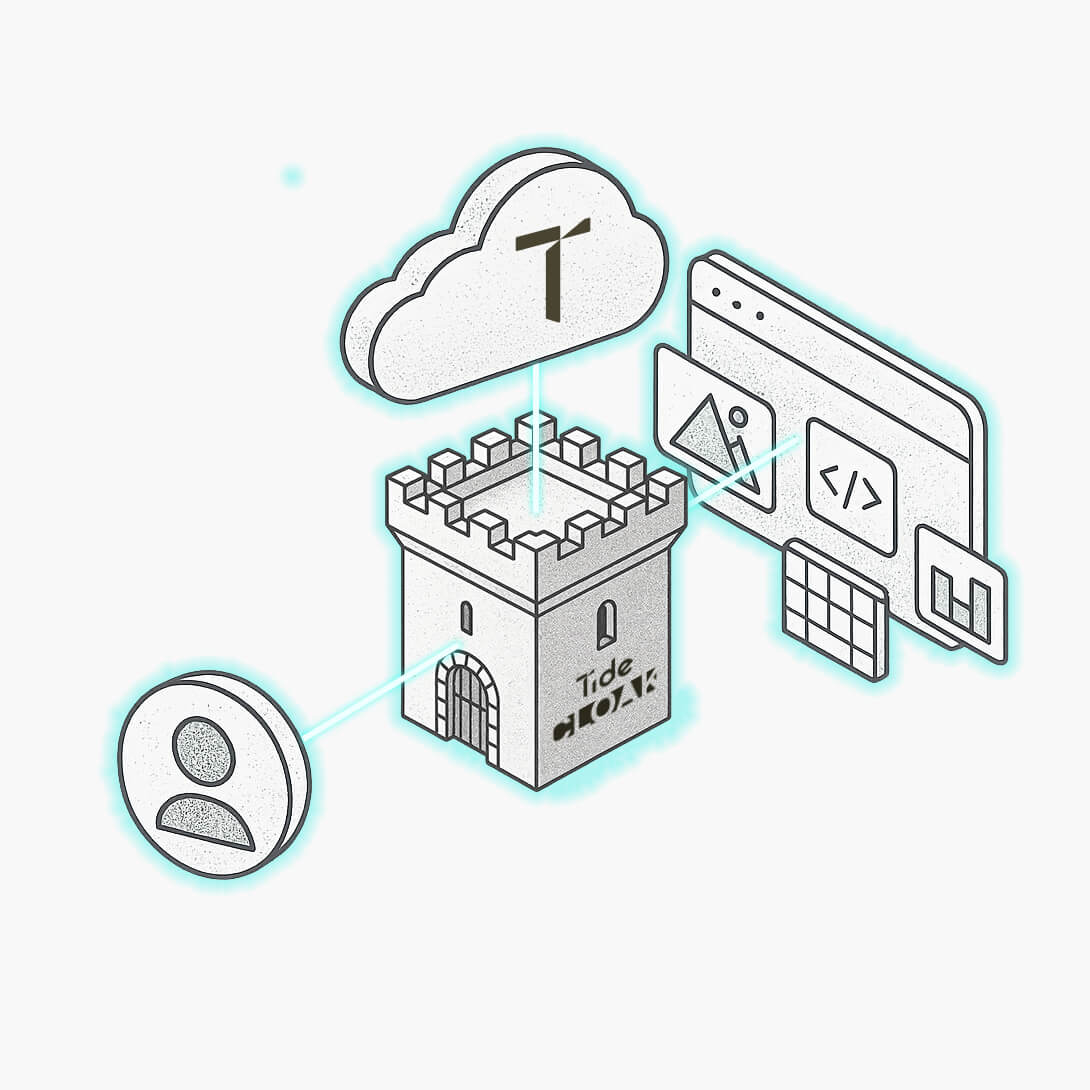
Robust users' authentication, authorization and authority management.
Developed in collaboration with leading cryptography researchers and global cybersecurity labs.
Awarded Research Council grant with Distinguished Professor Willy Susilo; Dr Dung Duong; Dr Fuchun Guo; Dr Shinsaku Kiyomoto; Dr Kazuhide Fukushima. Enabling Anonymity and Privacy in a Post-Quantum World.
Contributors and participants in national and global policy-making bodies. Cited in numerous policy recommendations and reports on future privacy protection.
Deeptech, cybersecurity and insurtech award winners.
InnovationAus 2024 Awards for Excellence, InsurTech Hartford Best Emerging InsurTech, AISA Startup of the Year, Tech23 Innovation Excellence Award, TechCrunch Disrupt Battlefield Finalist.



Published pioneering breakthrough research in secure multi-party computation, threshold cryptography, ZK proofs and confidential computing.
Featured in hundreds of leading publications and media outlets, such as Sky News, TechCrunch, Forbes, Financial Review, Dark Reading.
Supported by leading investors and partners who share our vision for a more secure digital future.